Network Penetration Testing
Selina ICT Offers Network Penetration Testing In Iraq. Deep-dive, manual network penetration testing performed by experienced and certified penetration testers
What is Network Penetration Testing?
The primary objective for a network penetration test is to identify exploitable vulnerabilities in networks, systems, hosts, and network devices (ie: routers, switches) before hackers can discover and exploit them. Network penetration testing will reveal real-world opportunities for hackers to be able to compromise systems and networks in such a way that allows for unauthorized access to sensitive data or even take-over systems for malicious/non-business purposes.

- Identify security flaws present in the environment
- Understand the level of risk for your organization
- Help address and fix identified network security flaws
Selina ICT Security network penetration testers have had experience supporting networks, systems, and hosts —not just trying to break them. They leverage this experience to zero in on critical issues and provide actionable remediation guidance.
Approach
Selina ICT Security’s network penetration testing service utilizes a comprehensive, risk-based approach to manually identify critical network-centric vulnerabilities that exist on all in-scope networks, systems, and hosts.
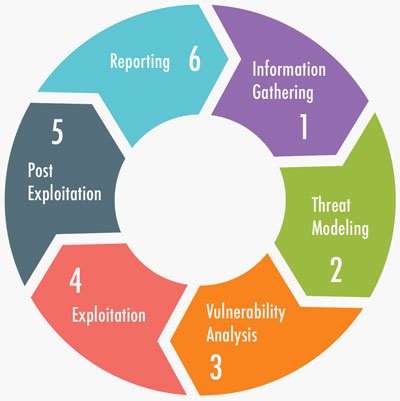
1. Information Gathering
2. Threat Modeling
3. Vulnerability Analysis
4. Exploitation
5. Post-Exploitation
6. Reporting
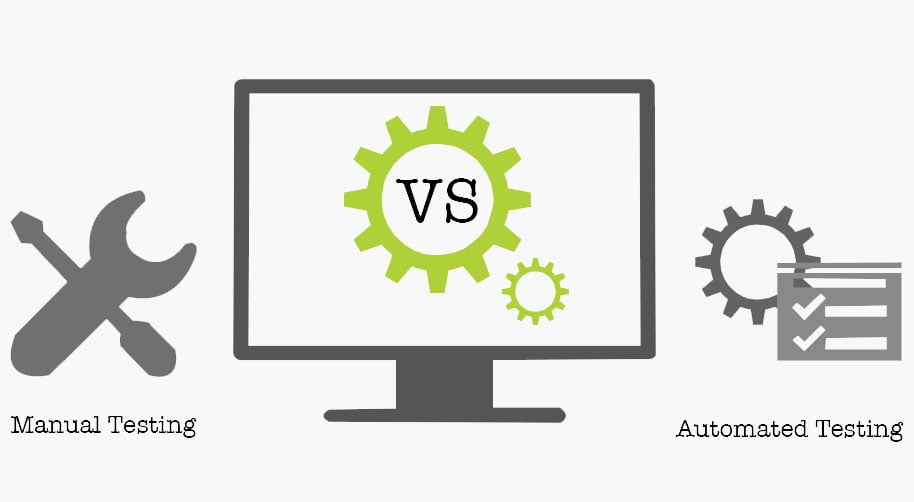
Manual Testing vs Automated Testing
Selina ICT’s approach consists of about 80% manual testing and about 20% automated testing – actual results may vary slightly. While automated testing enables efficiency, it is effective in providing efficiency only during the initial phases of a penetration test. At Selina ICT Security, we believe that an effective and comprehensive penetration test can only be realized through rigorous manual testing techniques.
Tools
To perform a comprehensive real-world assessment, Selina ICT Security utilizes commercial tools, internally developed tools, and the same tools that hackers use on every assessment. Once again, we intend to assess systems by simulating a real-world attack and we leverage the many tools at our disposal to effectively carry out that task.

Reporting
We consider the reporting phase to mark the beginning of our relationship. Selina ICT strives to provide the best possible customer experience and service. As a result, our report makes up only a small part of our deliverable. We provide clients with an online remediation knowledge base, dedicated remediation staff, and ticketing system to close the ever-important gap in the remediation process following the reporting phase.
We exist to not only find vulnerabilities but also to fix them.

Methodology
Every network penetration test is conducted consistently using globally accepted and industry-standard frameworks. To ensure a sound and comprehensive penetration test, Selina ICT leverages industry-standard frameworks as a foundation for carrying out penetration tests. At a minimum, the underlying framework is based on the Penetration Testing Execution Standard (PTES) but goes beyond the initial framework itself.
Intelligence Gathering
The information-gathering phase consists of service enumeration, network mapping, banner reconnaissance, and more. Host and service discovery efforts result in a compiled list of all accessible systems and their respective services to obtain as much information about the systems as possible.
Host and service discovery includes initial domain footprinting, live host detection, service enumeration, and operating system and application fingerprinting. The purpose of this step is to collectively map the in-scope environment and prepare for threat identification.


Threat Modeling
With the information collected from the previous step, security testing transitions to identifying vulnerabilities within systems. This begins with automated scans initially but quickly develops into deep-dive manual testing techniques. During the threat-modeling step, assets are identified and categorized into threat categories. These may involve: sensitive documents, trade secrets, financial information but more commonly consist of technical information found during the previous phase.
Vulnerability Analysis
The vulnerability analysis phase involves the documenting and analysis of vulnerabilities discovered as a result of the previous steps. This includes the analysis of out from the various security tools and manual testing techniques. At this point, a list of attractive vulnerabilities, suspicious services, and items worth researching further has been created and weighted for further analysis. In essence, the plan of attack is developed here.

Exploitation
Unlike a vulnerability assessment, a penetration test takes such a test quite a bit further specifically by way of exploitation. Exploitation involves actually carrying out the vulnerability’s exploit (ie: buffer overflow) to be certain if the vulnerability is truly exploitable. During a Selina ICT Security network penetration test, this phase consists of employing heavy manual testing tactics and is often quite time-intensive.
Reporting
The reporting step is intended to deliver, rank, and prioritize findings and generate a clear and actionable report, complete with evidence, to the project stakeholders. The presentation of findings can occur via Webex or in-person – whichever format is most conducive for communicating results. At Selina ICT Security, we consider this phase to be the most important and we take great care to ensure we’ve communicated the value of our service and findings thoroughly.

We’re not done yet…
We consider the reporting phase to mark the beginning of our relationship. Selina ICT strives to provide the best possible customer experience and service. As a result, our report makes up only a small part of our deliverable. We provide clients with an online remediation knowledge base, dedicated remediation staff, and ticketing system to close the ever-important gap in the remediation process following the reporting phase.
We exist to not only find vulnerabilities but also to fix them.
Deliverable
At Selina ICT Security, we consider the Delivery / Reporting phase to be the most important and we take great care to ensure we’ve communicated the value of our service and findings thoroughly. The deliverable consists of an electronic report that includes several key components including, but not limited to: Executive Summary, Scope, Findings, Evidence, Tools, and Methodology. In addition to the report, a raw file in comma-separated value (CSV) format is also provided to optimize the remediation and management of any identified findings.


